2014-11-13 - FIESTA EK FROM 205.234.186[.]110 - BETAMEDSEARCH[.]IN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP of the pcap: 2014-11-13-Fiesta-EK-traffic.pcap.zip 1.5 MB (1,515,122 bytes)
- ZIP of the malware: 2014-11-13-Fiesta-EK-malware.zip 463.6 kB (463,572 bytes)
NOTES:
- Since early- to mid-October 2014, the gate used by this actor (normally pointing to Fiesta EK) moved to 94.242.216[.]64.
- Currently, this gate leads to Fiesta EK from the 205.234.186[.]0/24 range. So far, I've seen 205.234.186[.]109 and 205.234.186[.]110.
- Because of recent changes in Fiesta, I'm not seeing as many EmergingThreats signatures as before; however, they still do a good job catching this exploit kit.
- I didn't see any VRT signatures trigger on today's Fiesta EK patterns, although VRT did catch the post-infection traffic.
BLOG ENTRIES ON FIESTA WITH CURRENT PATTERNS FROM THIS ACTOR:
- 2014-10-26 - Fiesta EK from 205.234.186[.]109 - hematitetekki[.]biz
- 2014-11-01 - Fiesta EK from 205.234.186[.]109 - conocarpusgeorgsimonohm[.]us
- 2014-11-13 - Fiesta EK from 205.234.186[.]110 - betamedsearch[.]in
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 69.167.176[.]10 - www.autogeekonline[.]net - Compromised website
- 94.242.216[.]64 - evgeneevich[.]com - Redirect/gate
- 205.234.186[.]110 - betamedsearch[.]in - Fiesta EK
- 79.142.66[.]239 - report.5i5qg5iq5w5u5m5[.]com - Post-infection traffic triggering Simda alerts
- 5.149.248[.]152 - report.5i5qg5iq5w5u5m5[.]com - Post-infection traffic triggering Simda alerts
- 5.149.248[.]152 - update.8kxkslrbaw[.]com - Post-infection traffic triggering Simda alerts
- 5.149.248[.]152 - update.roighh5[.]com - Post-infection traffic triggering Simda alerts
COMPROMISED WEBSITE AND REDIRECT:
- 2014-11-13 14:29:15 UTC - www.autogeekonline[.]net - GET /
- 2014-11-13 14:29:16 UTC - evgeneevich[.]com - GET /?JqE_1T=dzM68L8qt16uTdl&_3D=al8RXeLv1r8fhf&lnqwO=UbVSfM8jGfJaiP3t4j&CPW7g=dXK2W9gb30OaN&
ifY=t3ssf1W0qRd3Vi1
FIESTA EK:
- 2014-11-13 14:29:34 UTC - betamedsearch[.]in - GET /die9a2r1/imN1WB1xr70SFoh10hsP
- 2014-11-13 14:29:36 UTC - betamedsearch[.]in - GET /die9a2r1/36a0e651488d0fb80600580b570d0406030f58035e025701080355065155050606;120000;38
- 2014-11-13 14:29:38 UTC - betamedsearch[.]in - GET /die9a2r1/1ffdcd8fbfa33bf952160d5f515f0951015f5f5758505a560a5352525707085104;7
- 2014-11-13 14:29:44 UTC - betamedsearch[.]in - GET /die9a2r1/1ffdcd8fbfa33bf952160d5f515f0951015f5f5758505a560a5352525707085104;7;1
- 2014-11-13 14:29:46 UTC - betamedsearch[.]in - GET /die9a2r1/0ff8eb02b9304f66430a100357590105005f5f0b5e5652020b53520e5101000505;4060310
- 2014-11-13 14:29:50 UTC - betamedsearch[.]in - GET /die9a2r1/1f8cf5515dc1b13d5b085458540e0406015f01505d0157010a530c555256050604
- 2014-11-13 14:29:50 UTC - betamedsearch[.]in - GET /die9a2r1/24212c821bd141645346530a00580905020d0b0209575a02090106070600080507
- 2014-11-13 14:29:50 UTC - betamedsearch[.]in - GET /die9a2r1/33ea749fbfa33bf950430e5a050f0851030a5c520c005b56080651570357095106;5
- 2014-11-13 14:29:56 UTC - betamedsearch[.]in - GET /die9a2r1/33ea749fbfa33bf950430e5a050f0851030a5c520c005b56080651570357095106;5;1
- 2014-11-13 14:29:57 UTC - betamedsearch[.]in - GET /die9a2r1/46b24a99e839237c5b590009065a080e040f5b010f555b090f0356040002090101
- 2014-11-13 14:29:57 UTC - betamedsearch[.]in - GET /die9a2r1/24212c821bd141645346530a00580905020d0b0209575a02090106070600080507
- 2014-11-13 14:29:57 UTC - betamedsearch[.]in - GET /die9a2r1/46b24a99e839237c5b590009065a080e040f5b010f555b090f0356040002090101
- 2014-11-13 14:29:58 UTC - betamedsearch[.]in - GET /die9a2r1/24212c821bd141645346530a00580905020d0b0209575a02090106070600080507
- 2014-11-13 14:29:58 UTC - betamedsearch[.]in - GET /die9a2r1/24212c821bd141645346530a00580905020d0b0209575a02090106070600080507
- 2014-11-13 14:29:59 UTC - betamedsearch[.]in - GET /die9a2r1/1f8cf5515dc1b13d5b085458540e0406015f01505d0157010a530c555256050604
- 2014-11-13 14:30:00 UTC - betamedsearch[.]in - GET /die9a2r1/1f8cf5515dc1b13d5b085458540e0406015f01505d0157010a530c555256050604
POST-INFECTION TRAFFIC:
- 2014-11-13 14:29:44 UTC - report.5i5qg5iq5w5u5m5[.]com - GET /?c3sKUO31=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:29:45 UTC - report.5i5qg5iq5w5u5m5[.]com POST /
- 2014-11-13 14:29:45 UTC - update.8kxkslrbaw[.]com - GET /?rk=kayolpfanl6epN2j2aWlyMKplJeon9ek[long string of characters]
- 2014-11-13 14:29:46 UTC - report.5i5qg5iq5w5u5m5[.]com - GET /?E7a343=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:29:47 UTC - report.5i5qg5iq5w5u5m5[.]com - GET /?1oCE1a920=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:29:47 UTC - report.5i5qg5iq5w5u5m5[.]com - GET /?sK1yW312=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:14 UTC - report.5i5qg5iq5w5u5m5[.]com - GET /?17wS113=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:15 UTC - report.555aa555s5e55ku[.]com - GET /?5yWS5e531=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:16 UTC - report.555aa555s5e55ku[.]com POST /
- 2014-11-13 14:30:16 UTC - update.roighh5[.]com - GET /?5o=kayolpfanl7YqM6fzqFolMSh06mplsOonWa[long string of characters]
- 2014-11-13 14:30:16 UTC - report.555aa555s5e55ku[.]com - GET /?7u31i9q43=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:17 UTC - report.555aa555s5e55ku[.]com - GET /?31qG330=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:17 UTC - report.555aa555s5e55ku[.]com - GET /?7931c9317=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:17 UTC - report.555aa555s5e55ku[.]com - GET /?9gM7958=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:18 UTC - report.555aa555s5e55ku[.]com - GET /?55uOC55=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:23 UTC - report.555aa555s5e55ku[.]com - GET /?93mY916=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:34 UTC - report.555aa555s5e55ku[.]com - GET /?1c93uO909=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:45 UTC - www.bing[.]com - GET /chrome/report.html?K79g=%9B%EE%EDk%D9%DF%A5%8D%[long string of characters]
- 2014-11-13 14:30:46 UTC - report.555aa555s5e55ku[.]com - GET /?SK3y25=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:46 UTC - report.555aa555s5e55ku[.]com - GET /?55aAA5k57=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:46 UTC - report.555aa555s5e55ku[.]com - GET /?555q563=%96%9C%A8%A1%A8%DAge%[long string of characters]
- 2014-11-13 14:30:47 UTC - report.555aa555s5e55ku[.]com - GET /?yW7u3m18=%96%9C%A8%A1%A8%DAge%[long string of characters]
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-11-13-Fiesta-EK-flash-exploit.swf
File size: 9,985 bytes
MD5 hash: 02b2aded61ec929eb8eab6302d51e707
Detection ratio: 3 / 53
First submission: 2014-11-10 17:18:49 UTC
VirusTotal link: https://www.virustotal.com/en/file/ab0a02f5c802bd38fc04d2764492a42cfe5016c8242b58453686200fbe208e80/analysis/
JAVA EXPLOIT
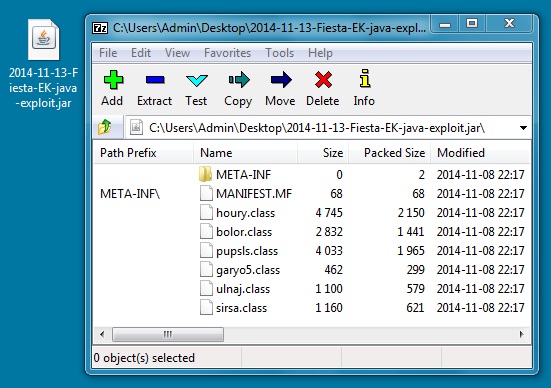
File name: 2014-11-13-Fiesta-EK-java-exploit.jar
File size: 8,085 bytes
MD5 hash: 4ae884b9caa02524fab8bdd248dec92f
Detection ratio: 4 / 54
First submission: 2014-11-13 15:44:58 UTC
VirusTotal link: https://www.virustotal.com/en/file/10973e16a16ad7c195634e26bc24ca3cbdab5abf8fc7ebda04159f2b6f5cb2d7/analysis/
SILVERLIGHT EXPLOIT
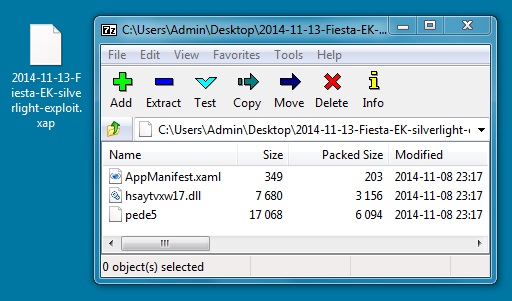
File name: 2014-11-13-Fiesta-EK-silverlight-exploit.xap
File size: 9,773 bytes
MD5 hash: 457c896b32cbf52db3397953bc26efee
Detection ratio: 5 / 55
First submission: 2014-11-13 15:45:14 UTC
VirusTotal link: https://www.virustotal.com/en/file/718f92a945837ea7a11278db19733d42cb38b393dc17a8167a2eeb7657261496/analysis/
MALWARE PAYLOAD
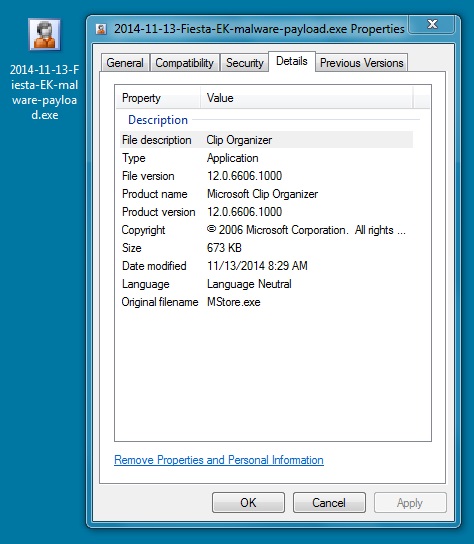
File name: 2014-11-13-Fiesta-EK-malware-payload.exe
File size: 689,152 bytes
MD5 hash: 03384d3b5731e29d9345f274efce3653
Detection ratio: 3 / 52
First submission: 2014-11-13 15:45:52 UTC
VirusTotal link: https://www.virustotal.com/en/file/8737344b728c4245c0ca89f884de1fea2e6fda328673166c2ba171ada12d612c/analysis/
SNORT EVENTS
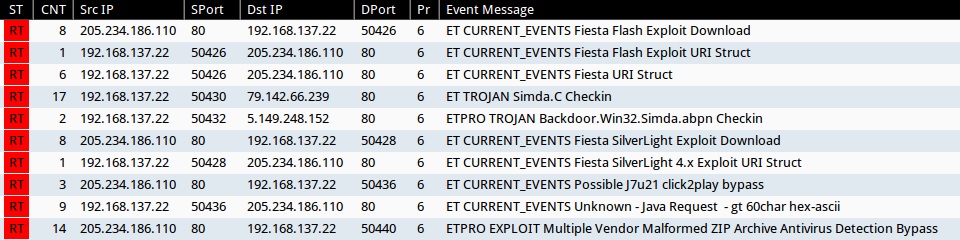
Emerging Threats and ETPRO rulesets from Sguil after using tcpreplay on the pcap in Security Onion (not including ET INFO or ET POLICY rules):
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Fiesta Flash Exploit Download (sid:2018411)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Fiesta Flash Exploit URI Struct (sid:2019612)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Fiesta URI Struct (sid:2018407)
- 79.142.66[.]239:80 - ET TROJAN Simda.C Checkin (sid:2016300)
- 5.149.248[.]152:80 - ETPRO TROJAN Backdoor.Win32.Simda.abpn Checkin (sid:2807145)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Fiesta SilverLight 4.x Exploit URI Struct (sid:2019623)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Fiesta SilverLight Exploit Download (sid:2018409)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass (sid:2017509)
- 205.234.186[.]110:80 - ET CURRENT_EVENTS Unknown - Java Request - gt 60char hex-ascii (sid:2014912)
- 205.234.186[.]110:80 - ETPRO EXPLOIT Multiple Vendor Malformed ZIP Archive Antivirus Detection Bypass (sid:2800029)
Signature hits from the Sourcefire VRT ruleset after reading the pcap in Snort 2.9.6.2 on Debian 7:
- 2014-11-13 14:29:16 UTC - 69.167.176[.]10:80 - [1:32481:1] POLICY-OTHER Remote non-JavaScript file found in script tag src attribute
- 2014-11-13 14:29:16 UTC - 69.167.176[.]10:80 - [120:6:1] (http_inspect) HTTP RESPONSE GZIP DECOMPRESSION FAILED
- 2014-11-13 14:29:41 UTC - 205.234.186[.]110 - [139:1:1] (spp_sdf) SDF Combination Alert (x2)
- 2014-11-13 14:29:44 UTC - 79.142.66[.]239:80 - [1:22937:5] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection (x17)
- 2014-11-13 14:29:45 UTC - 5.149.248[.]152:80 - [1:26212:2] MALWARE-CNC Win.Trojan.Proxyier variant outbound connection (x2)
- 2014-11-13 14:30:45 UTC - 204.79.197[.]200:80 - [1:20661:4] MALWARE-CNC Simbda variant outbound connection
SCREENSHOTS FROM THE TRAFFIC
Malicious javascript in page from compromised website:
Redirect (gate) pointing to Fiesta EK:
Click here to return to the main page.