2016-02-07 - RIG EK FROM 188.227.16[.]59
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-02-07-Rig-EK-traffic-2-pcaps.zip 623.9 kB (623,915 bytes)
- 2016-02-07-Rig-EK-malware-and-artifacts.zip 500.3 kB (500,328 bytes)
NOTES:
- This is the same actor that's been using Rig EK to deliver Qbot (Qakbot). I first noticed it in Mid-December 2015 and have occasionally seen it since then.
- https://isc.sans.edu/diary/Actor+using+Rig+EK+to+deliver+Qbot/20513
- https://isc.sans.edu/diary/Actor+using+Rig+EK+to+deliver+Qbot+update/20551
- https://www.malware-traffic-analysis.net/2015/12/31/index.html
- https://www.malware-traffic-analysis.net/2016/01/11/index.html
- https://www.malware-traffic-analysis.net/2016/01/28/index.html
- About a month ago, David Ferguson emailed me a Python script he'd wrote to extract the Rig EK landing page URL from the .php text returned by this actor's gate.
- I've included a copy of David's Python script (RigC2finder-pythonV2.py) in today's .zip archive that contains the malware and artifacts.
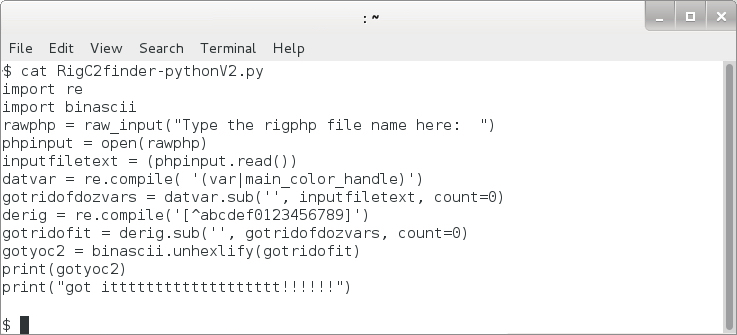
Shown above: David's Python script.
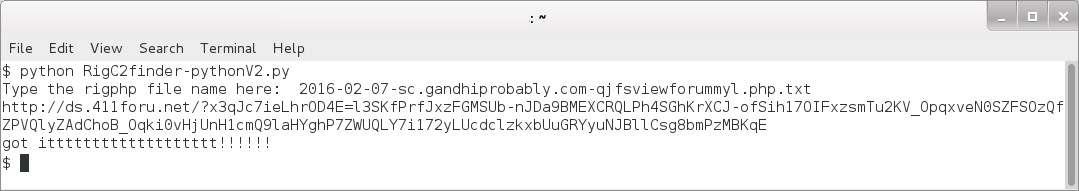
Shown above: David's Python script in action.
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- www.engeniusforum[.]com - Compromised website
- 192.185.21[.]183 port 80 - sc.gandhiprobably[.]com - Gate/redirect
- 188.227.16[.]59 port 80 - ds.411foru[.]net - Rig EK
TRAFFIC - FIRST RUN:
- 2016-02-07 16:05:14 UTC - www.engeniusforum[.]com - GET /
- 2016-02-07 16:05:14 UTC - www.engeniusforum[.]com - GET /assets/javascript/jquery.min.js?assets_version=5
- 2016-02-07 16:05:15 UTC - sc.gandhiprobably[.]com - GET /pymuviewforumil.php
- 2016-02-07 16:05:17 UTC - ds.411foru[.]net - GET /?wHeLf7iaJBvMDYU=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OI
FxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfEQuU721XzzbNGJckkzxWKvDNQnehIVwgUtQwXnvzNBKqE
- 2016-02-07 16:05:18 UTC - ds.411foru[.]net - GET /index.php?wHeLf7iaJBvMDYU=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfEQuU721XzzbNGJckkzxWKvDNQnehIVwgUtQwXnvzN
BKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PN2nZYmmA
- 2016-02-07 16:05:18 UTC - ds.411foru[.]net - GET /index.php?wHeLf7iaJBvMDYU=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZfEQuU721XzzbNGJckkzxWKvDNQnehIVwgUtQwXnvzN
BKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PV0mZxg
TRAFFIC - SECOND RUN:
- 2016-02-07 16:16:14 UTC - www.engeniusforum[.]com - GET /
- 2016-02-07 16:16:15 UTC - www.engeniusforum[.]com - GET /assets/javascript/jquery.min.js?assets_version=5
- 2016-02-07 16:16:15 UTC - sc.gandhiprobably[.]com - GET /qjfsviewforummyl.php
- 2016-02-07 16:16:16 UTC - ds.411foru[.]net - GET /?x3qJc7ieLhrOD4E=l3SKfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-ofSih17OI
FxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZWUQLY7i172yLUcdclzkxbUuGRYyuNJBllCsg8bmPzMBKqE
- 2016-02-07 16:16:18 UTC - ds.411foru[.]net - GET /index.php?x3qJc7ieLhrOD4E=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZWUQLY7i172yLUcdclzkxbUuGRYyuNJBllCsg8bmPzM
BKqKp0N6RgBnEB_CbJQlqw-BF3H6PXl5gv2pHn4oieWX_PB8npMmmA
- 2016-02-07 16:16:19 UTC - ds.411foru[.]net - GET /index.php?x3qJc7ieLhrOD4E=l3SMfPrfJxzFGMSUb-nJDa9BMEXCRQLPh4SGhKrXCJ-
ofSih17OIFxzsmTu2KV_OpqxveN0SZFSOzQfZPVQlyZAdChoB_Oqki0vHjUnH1cmQ9laHYghP7ZWUQLY7i172yLUcdclzkxbUuGRYyuNJBllCsg8bmPzM
BKqKp0N6RgBnEB_CbJQlqw-fECT6PXl5gv2pHn4oieWX_PV9lZUs3lM&dop=2
PRELIMINARY MALWARE ANALYSIS
RIG EK FLASH EXPLOIT:
File name: 2016-02-07-Rig-EK-flash-exploit.swf
File size: 14,495 bytes
MD5 hash: 90f9d6152503753e797f5e136fdbb29a
SHA1 hash: e4cf4ae7cc3ed19cc52bf1cc2304601a735fa0df
SHA256 hash: f871786c1cc03acce099dcc06475ead477846e7fc70a1f5c3bb4e0a6786993fe
Detection ratio: 5 / 54
First submission to VirusTotal: 2016-02-04 15:12:07 UTC
EK PAYLOAD:
File name: 2016-02-07-Rig-EK-malware-payload.exe
File size: 479,232 bytes
MD5 hash: b49df900e6e30636b632efd158697809
SHA1 hash: 65238b497170b921305fbdfb74101fbb6af6adc8
SHA256 hash: fb42468405a0c490efa803ac1bdf8ea024e33d29aeda00eddeba0bf85d278b43
Detection ratio: 15 / 54
First submission to VirusTotal: 2016-02-07 17:00:53 UTC
IMAGES

Shown above: Injected script appended to one of the .js files from the compromised website.
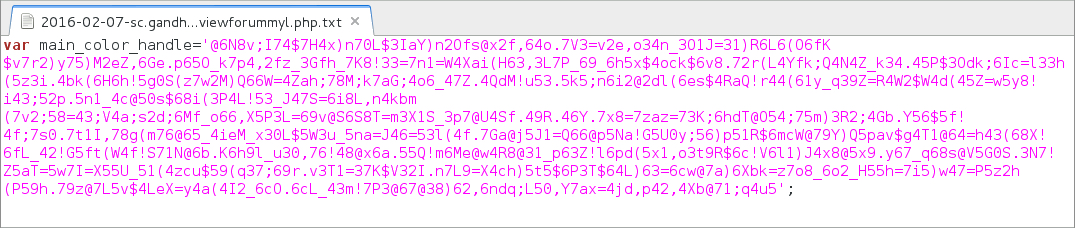
Shown above: main_color_handle variable returned from the gate used by this actor.
Click here to return to the main page.

