2017-06-06 - ROUGHTED CAMPAIGN RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2017-06-06-RoughTed-Rig-EK-2-pcaps.zip 1.5 MB (1,468,353 bytes)
- 2017-06-06-RoughTed-Rig-EK-sends-Chthonic-1st-run.pcap (304,404 bytes)
- 2017-06-06-RoughTed-Rig-EK-sends-Chthonic-2nd-run.pcap (1,290,703 bytes)
- 2017-06-06-RoughTed-Rig-EK-malware-and-artifacts.zip 239.6 kB (239,612 bytes)
- 2017-06-06-Rig-EK-artifact-o32.tmp-both-runs.txt (1,141 bytes)
- 2017-06-06-Rig-EK-flash-exploit-both-runs.swf (16,468 bytes)
- 2017-06-06-Rig-EK-landing-page-1st-run.txt (118,864 bytes)
- 2017-06-06-Rig-EK-landing-page-2nd-run.txt (32,831 bytes)
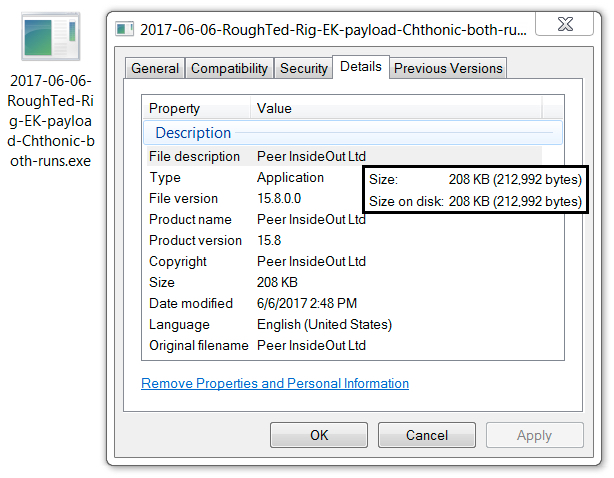
- 2017-06-06-RoughTed-Rig-EK-payload-Chthonic-both-runs.exe (212,992 bytes)
NOTES:
- Got the referrer from a blog post by @Zerophage1337 earlier today titled: Rig EK Via RoughTed Delivers Chthonic
- More on the RoughTed campaign from the MalwareBytes Blog at: RoughTed: the anti ad-blocker malvertiser
- This week, Rig EK is back to using Flash exploits, after it stopped using them for about 2 or 3 days late last week (example).
TRAFFIC
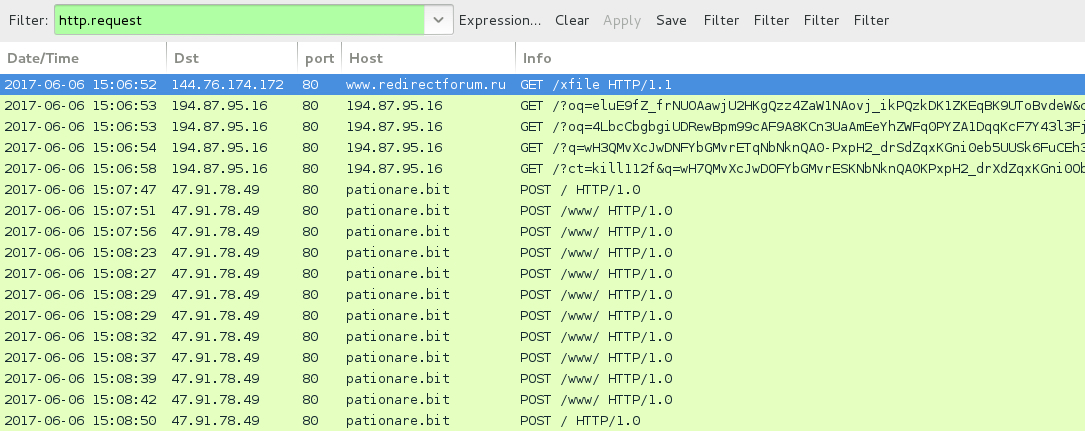
Shown above: Traffic from the second infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 144.76.174[.]172 port 80 - www.redirectforum[.]ru - GET /xfile [RoughTed-style gate leading to Rig EK]
- 194.87.95[.]16 port 80 - 194.87.95[.]16 - Rig EK (both runs)
- 47.91.78[.]49 port 80 - pationare[.]bit - Chthonic post-infection HTTP traffic
- 23.94.5[.]133 TCP port 53 - DNS query for pationare[.]bit
- 45.32.28[.]232 TCP port 53 - DNS query for pationare[.]bit
- 45.56.117[.]118 TCP port 53 - DNS query for pationare[.]bit
- 87.98.175[.]85 TCP port 53 - DNS query for pationare[.]bit
- 93.170.96[.]235 TCP port 53 - DNS query for pationare[.]bit
- 108.61[.]164.218 TCP port 53 - DNS query for pationare[.]bit
- 188.165[.]200.156 TCP port 53 - DNS query for pationare[.]bit
- 45.63.99[.]180 TCP port 53 - attempted TCP connection but RST from the server
- 141.138.157[.]53 TCP port 53 - attempted TCP connection but RST from the server
MALWARE
RIG EK FLASH EXPLOIT:
- SHA256 hash: 9fc5fb99f72be24ec7d1e2004f1c1f2083885059e0e072314cb712934415bc24
File size: 16,468 bytes
File description: Rig EK Flash exploit seen on 2017-06-06
MALWARE RETRIEVED FROM THE INFECTED HOST:
- SHA256 hash: 0434a5b69bea3a10443c0740bca4f36772cf67130c6b7da5b1b16494b3e12377
File location: C:\Users\[username]\AppData\Local\Temp\[random characters].tmp
File location: C:\Users\[username]\AppData\Roaming\Microsoft Visual Studio\MicrosoftVisualStudioM.exe
File location: C:\Users\[username]\AppData\Roaming\Windows Media Player\WindowsMediaPlayerU.exe
File size: 212,992 bytes
File description: Chthonic banking Trojan
Shown above: Metadata on today's Chthonic banking Trojan sample.
WINDOWS REGISTRY CHANGES FOR PERSISTENCE:
- Key name: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Value name: MicrosoftVisualStudioM
Value type: REG_SZ
Value data: C:\Users\[username]\AppData\Roaming\Microsoft Visual Studio\MicrosoftVisualStudioM.exe
- Value name: WindowsMediaPlayerU
Value type: REG_SZ
Value data: C:\Users\[username]\AppData\Roaming\Windows Media Player\WindowsMediaPlayerU.exe
Click here to return to the main page.