2014-05-02 - MAGNITUDE EK FROM 193.169.245[.]11 - NAUGHTYGAINING[.]NET
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
NOTES:
- This one's a relatively quick post for situational awareness. I didn't extract or deobfuscate any of the malware from the pcap.
- My previous entry on Angler EK had a click fraud-style trojan, and one of the fake search sites was the10search[.]net.
- That site returned an .htaccess style 302 redirect to Magnitude EK.
- I typed the fake search site's domain name into a web browser, and it took me there--no referrer was needed.
PREVIOUS MAGNITUDE EK:
- 2014-01-14 - Magnitude EK from 66.55.140[.]115 - 73373e4.13f8.0caad.991f.004.a8a.5d1.1f0.sknhzkfjldkp.lunchdoors[.]pw
- 2014-03-12 - Magnitude EK from 67.196.49[.]168 - 6b0543.e3fb5.c8.5b9.b0fc2e9.53.cd0.b7.df.unnujshair.smallestpieces[.]pw
- 2014-03-23 - Magnitude EK from 67.196.50[.]153 - 27.e97a7fd.4e.15b.6f7.ca0726.6f2744.f70.pidzfnbzozvj.pendates[.]in
- 2014-03-25 - Magnitude EK from 67.196.50[.]155 - 3ee0b.6b5.ed93d77.9e88.d4f0e.cf49a.79f.hsyeekqwnyd.dumprelated[.]in
- 2014-04-14 - Magnitude EK from 67.196.3[.]65 - 9b5ef08.e9b.1c34d5.379b.0078.5638.0cd0.rpaitxocww.dumpequally.net
- 2014-04-15 - Magnitude EK from 67.196.3[.]66 - 44d.c07.5d7.5ce6.17c4.96d.0038dec.aeea6.ujxadmcithxz.suggestinglots[.]in
- 2014-04-16 - Magnitude EK from 67.196.3[.]67 - 40909.e877985.75beb1.3126.2759.b7f5b.3.ymxgizns.poundswhose[.]in
- 2014-04-17 - Magnitude EK from 67.196.3[.]69 - b33715e.1f.de4ce9b.1ed.d0303ec.b7d939.yccgnkggdknu.referredknew[.]in
- 2014-04-26 - Magnitude EK from 193.169.245[.]5 - 2decc.1a9d.d3.f93b0bf.a9c.efe7f.64f6d5.yfbxhpbig.feelchips[.]in
- 2014-04-30 - Magnitude EK from 193.169.245[.]10 - 5cfe1.df.0572.77bbe0.d22.4a03.29246d.0c.hjyagwtu.safehe[.]in
- 2014-05-01 - Magnitude EK from 193.169.245[.]10 - e2f.18.bc5.465f.90.33c10.26.1e098.26.efee.motbypqfa.afternoonride[.]pw
- 2014-05-02 - Magnitude EK from 193.169.245[.]11 - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net
CHAIN OF EVENTS
ASSOCIATED DOMAINS:
- 212.38.166[.]89 - the10search[.]net - Compromised website
- 193.169.245[.]11 - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - Magnitude EK
COMPROMISED WEBSITE:
- 06:01:42 UTC - 212.38.166[.]89 - the10search[.]net - GET /
MAGNITUDE EK:
- 06:01:43 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /
- 06:01:48 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/38b33162224f59ebfc2dad03d288d790
- 06:01:50 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /favicon.ico
- 06:02:02 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/58702b843234284357c133ce034651db
- 06:02:02 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/ea967d07221e1d239ce7dcc3e5219489
- 06:02:03 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/ea967d07221e1d239ce7dcc3e5219489
- 06:02:03 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/58ed00f510627b5e0fffad4f0d28ebf1
- 06:02:03 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/58ed00f510627b5e0fffad4f0d28ebf1
- 06:02:04 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/ea967d07221e1d239ce7dcc3e5219489
- 06:02:05 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/ea967d07221e1d239ce7dcc3e5219489
- 06:02:05 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/0
- 06:02:06 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/qz.class
- 06:02:07 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/qz.class
- 06:02:08 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/qz.class
- 06:02:08 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/1
- 06:02:09 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/qz.class
- 06:02:09 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/2
- 06:02:10 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/3
- 06:02:13 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/4
- 06:02:19 UTC - c462.81d9.3b311.283f0fd.3f5ea.966.8d.99.qqmytmmh.naughtygaining[.]net - GET /9f4f573499a11745c24548eb934e4496/5
SOME OF THE POST-INFECTION TRAFFIC:
- 06:02:14 UTC - 46.160.212[.]27 - biobetic-new[.]com - GET /b/shoe/749634
- 06:02:16 UTC - 46.160.212[.]27 - biobetic-new[.]com - GET /b/shoe/749634
- 06:02:23 UTC - 46.160.212[.]27 - biobetic-new[.]com - GET /b/shoe/749634
- 06:02:27 UTC - 46.160.212[.]27 - revolution-start[.]com - GET /components-i75.89/jquery/ [Repeats several times]
- 06:03:42 UTC - 173.194.127[.]240 - www.google[.]com - GET /
- 06:03:46 UTC - 108.59.251[.]118 - aoneteleshop[.]com - GET /images/dummy/heap170id3.exe
ALERTS
ALERTS FOR THE INFECTION TRAFFIC (from Sguil on Security Onion)
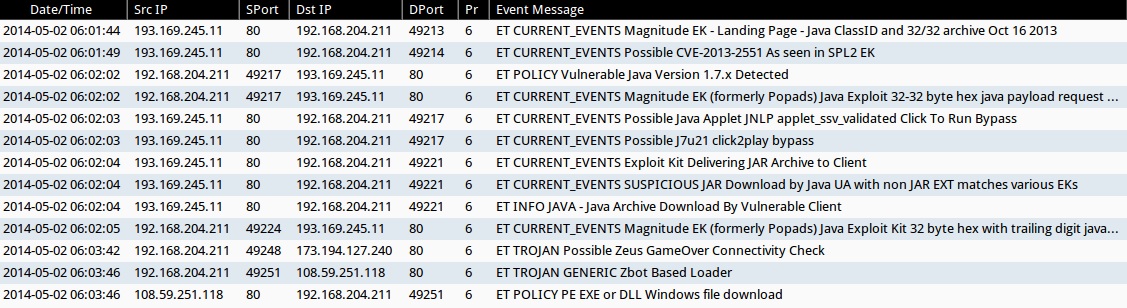
- 2014-05-02 06:01:44 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Magnitude EK - Landing Page - Java ClassID and 32/32 archive Oct 16 2013
- 2014-05-02 06:01:49 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Possible CVE-2013-2551 As seen in SPL2 EK
- 2014-05-02 06:02:02 UTC - 193.169.245[.]11:80 - ET POLICY Vulnerable Java Version 1.7.x Detected
- 2014-05-02 06:02:02 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit 32-32 byte hex java payload request Oct 16 2013
- 2014-05-02 06:02:03 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Possible Java Applet JNLP applet_ssv_validated Click To Run Bypass
- 2014-05-02 06:02:03 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Possible J7u21 click2play bypass
- 2014-05-02 06:02:04 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Exploit Kit Delivering JAR Archive to Client
- 2014-05-02 06:02:04 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS SUSPICIOUS JAR Download by Java UA with non JAR EXT matches various EKs
- 2014-05-02 06:02:04 UTC - 193.169.245[.]11:80 - ET INFO JAVA - Java Archive Download By Vulnerable Client
- 2014-05-02 06:02:05 UTC - 193.169.245[.]11:80 - ET CURRENT_EVENTS Magnitude EK (formerly Popads) Java Exploit Kit 32 byte hex with trailing digit java payload request
- 2014-05-02 06:03:42 UTC - 173.194.127[.]240:80 - ET TROJAN Possible Zeus GameOver Connectivity Check
- 2014-05-02 06:03:46 UTC - 108.59.251[.]118:80 - ET TROJAN GENERIC Zbot Based Loader
- 2014-05-02 06:03:46 UTC - 108.59.251[.]118:80 - ET POLICY PE EXE or DLL Windows file download
Click here to return to the main page.
